Wired or Wireless
1 Charge = 1 Year
Waterproof IP66
Live Streaming
Full HD 1080p
TSCM – Technical Surveillance Counter Measures
THE THREATS ARE REAL
The quest for illicit intelligence is a never-ending threat; from criminals trying to obtain information for financial gain, to sophisticated state-sponsored adversaries looking for political and military gains. While we do not always know what kind of threats are around us, a robust security policy encompassing physical security, cyber security and protection from electronic surveillance is needed to ensure secrets remain secret. The security of your building, your Sensitive Compartmented Information Facility (SCIF), your private conversations, your plans and secrets can all be compromised by surveillance devices; from small, inexpensive GSM/UMTS bugs to bespoke devices created by state actors.
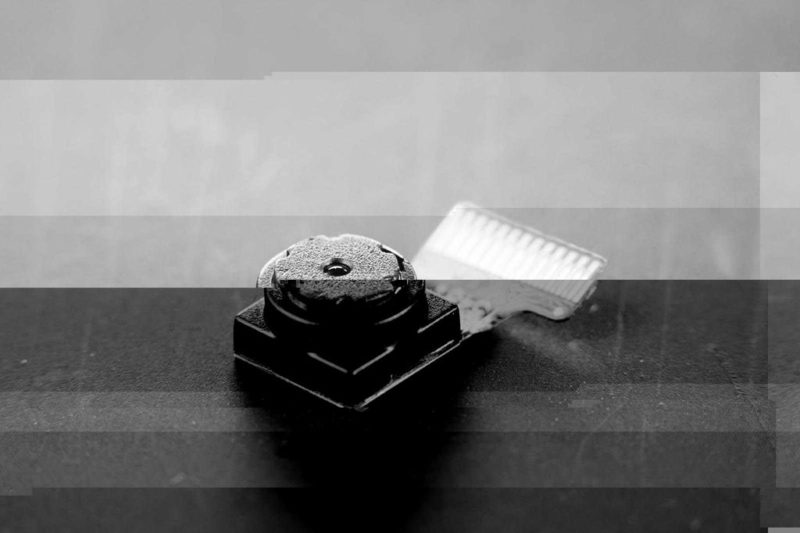
Devices can be difficult to locate
Modern surveillance technologies are highly discreet, highly capable, and very difficult to locate. Even the smallest device can pack a considerable amount of technology. These devices can be integrated into USB cables, light bulbs, or any number of other common objects. When not in use, such a device can lie dormant. If connected to a mobile network, it may only need to “shake hands” momentarily once every 8 hours (network defined); at other times it remains RF invisible.
Without good OPSEC (Operational Security), undetected RF surveillance and data transmissions can allow an adversary to:
- Conduct ISR operations against the organization
- Collect and disclose classified information
- Hijack critical C2 signals that can cause loss of finances, assets, or even life
- Obtain money and financial data
- Compromise law enforcement and intelligence agency operations
Layered Approach
The way to counter technical surveillance is to adopt a multi-layered approach to security
Bespoke RF Attack: IPMS
In-Place Monitoring Systems Persistent wide-band threat monitoring, alert and intelligence gathering - Bespoke threats
Common Attack: WIDS
Wireless Intrusion Detection Sys. Continuous cyber-threat assessment of common wireless devices
Physical Attack Sweep Teams
Manual Search, Targeted assessment room by room
Physical Security, Building, Environment
Physical security process, construction location
Layers







What we do
Our RF monitoring and geolocation systems can be used in multiple applications to help detect, identify/classify, manage and locate RF signals of interest in a range of complex spectrum environments – capturing and turning RF data into actionable intelligence.

Bug sweeping
The traditional approach to detecting electronic surveillance devices is to use a hand-held bug sweeping tool. This tool is moved through a room to scan for the presence of a bug. They can be highly effective; however, bugs are often able to evade these sweeps only transmitting in short, infrequent bursts or frequency hopping, transmissions are “hidden” close to a high-power signal or simply because the bug has been placed after a sweep has been conducted. Sweeps are also time consuming and extremely disruptive, so much so that many organizations only carry them out periodically. TSCM Sweeps are an intrinsic element of technical security, and support both WIDS and IPMS strategies.
Wireless Intrusion Detection Systems (WIDS)
WIDS are cellphone, Wi-Fi, and Bluetooth monitoring systems. They can detect and identify the presence and sometimes locations, of a device such as a cellphone or a bug transmitting on the cellphone network. They are great for enforcing a no cellphone policy or black/whitelisting certain devices in the facility. While WIDS certainly have a valuable role to play in TSCM they often operate within a limited frequency range, typically up to 6GHz. To provide complete assurance against RF surveillance, there is a need for continuous, wideband TSCM in the form of an In-Place Monitoring System. This is where the RFeye Guard system comes in.
In-Place Monitoring System (IPMS)
RFeye Guard is a continuous TSCM In-Place Monitoring System (IPMS). It continuously monitors the RF environment 24 hours a day, 365 days a year to instantly detect suspect signals, up to 40GHz, in real time. Even if a device transmits at 2am for less than a second, RFeye Guard will be able to detect it. Fast sweep speeds and exceptionally low noise figures allow the RFeye sensors to detect even the lowest-power and shortest-duration signals. These intelligent sensors, combined with the Guard software suite, operate autonomously and when a signal is detected, the RFeye Guard system can provide a real-time alert and location to a security guard.Protection against intruders, fires, water & more for every window, room and door
Nascetur ac malesuada natoque pulvinar pellentesque odio. Rhoncus dictumst taciti justo donec consectetuer metus. Amet vestibulum iaculis donec porta nam eget vitae natoque id.
- Smart Home Security
- Professional Installation
- In Home Consultation
- Doorbell Video Cameras
- Burglary Sensor Detection
- 24/7 Alarm Monitoring

Spectrum management and monitoring
Military spectrum management
DroneDefense
Air Defence
Critical Infrastructure Protection
Border Security
DF and Geo location
Counter Surveillance
RF Solutions
The electromagnetic spectrum is used in everything from voice and data communications to radar and navigation. CRFS hardware and software can be used to monitor and manage the RF Spectrum in a range of application settings, both military and civilian. Below are some of the key areas we work in, but if you have an application not listed, contact us to see how we can help.
Digital Threats
A malicious act that seeks to damage data, steal data, or disrupt digital life in general. Cyber-attacks include threats like computer viruses, data breaches, and Denial of Service (DoS) attacks.

Video surveillance
Video may be gathered for any number of reasons, for example, identifying people, observing security measures or capturing passwords on air-gapped devices, or for use as leverage in blackmail or social engineering. Common uses of video surveillance include observing the public at the entry to sports events, public transportation (train platforms, airports, etc.). If it is possible to identify schedules when security trends have occurred or may be likely to occur, that is also helpful to the process. One such application is for train platforms.
Data exfiltration
Data may be targeted by interception of keystrokes or installation of Wireless Advanced Persistent Threats (WAPT) devices that give remote "at-desk" access to a compromised computer, allowing for file transmission, network alteration, or data destruction.It can be difficult to detect. As it involves the transfer or moving of data within and outside a company’s network, it often closely resembles of mimics typical network traffic, allowing substantial data loss incidents to fly under the radar until data exfiltration has already been achieved.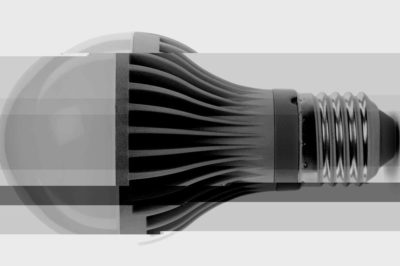
Audio surveillance
Audio intelligence can reveal a lot of information in a short time. It is generally immediate and context-based. Audio eavesdropping is not just limited to the transmission or buffer transmission of sound files. Modern devices allow for speech recognition, meaning only small text files need to be transmitted, very quickly, and at intervals of maybe weeks or longer. The ability of a device to remotely listen, overhear, record, and amplify in one location to another device in another location, a voice monitoring , sometimes called “Listen-In”Secure facilities & SCIFs 


Physical securityBug sweepingIn-place monitoring system
SCIFWhen matters of state and national security are being discussed, secrets need to remain secret. Often, these
 discussions will take place in a Sensitive Compartmented Information Facility (SCIF). A SCIF is an enclosed area (could be a room or an entire building) that is designed to protect occupants from surveillance. They are acoustically and electronically shielded and often guarded. Electronic devices such as phones or laptops are not permitted in these areas and have to be left outside.
discussions will take place in a Sensitive Compartmented Information Facility (SCIF). A SCIF is an enclosed area (could be a room or an entire building) that is designed to protect occupants from surveillance. They are acoustically and electronically shielded and often guarded. Electronic devices such as phones or laptops are not permitted in these areas and have to be left outside.
Why In-Place Monitoring?
If a phone or surveillance device was taken into a SCIF, by accident or maliciously, a previous TSCM sweep wouldn’t be effective. Security breaches need to be picked up the instant they happen, not hours or days later. An in-place monitoring system like RFeye Guard would be able to detect any device transmitting inside the SCIF the instance it happened, regardless of whether the device was brought in before or during the meeting. With RFeye Guard the security team can be immediately alerted, and the exact room the security breach occurred pinpointed. The meeting could be stopped before conversations are potentially compromised.
Embassies and diplomatic buildings 



In a world of constantly shifting social and political landscapes, it is important that nations have safe spaces to discuss ongoing events and policy both at home and outside home borders. Safe spaces must exist without fear of bugging, interception or eavesdropping technologies. These secure spaces exist within government buildings as well as embassies and other diplomatic buildings such as diplomatic residences. These environments need a solution to ensure those spaces are continually free from transmitting devices and assure absolute freedom to discuss ongoing policy, strategy or intelligence.
Why In-Place Monitoring?
These buildings need to have complete assurance against eavesdropping and other cyber and electromagnetic threats. An occasional TSCM sweep does not usually provide the peace of mind required since it is easy for devices to be switched off or moved during a sweep and reactivated ahead of an important meeting. Hostile actors are then able to gain information to be used in a manner detrimental to the nation’s security or prosperity. In such a scenario the device may be long gone before the data breach is recognized, leaving investigators unable to identify the source or prevent further breaches. Either way, identifying the damage has already been done.
RFeye Guard will autonomously monitor secure government buildings 24/7. This means a surveillance device planted immediately before a sensitive meeting will immediately generate an alarm with a location. Not only does this allow the meeting to be secured, but cross-referencing of RFeye Guard location data with CCTV or other data sources will often allow the responsible person to be identified.
The state-of-the-art software and RF specifications of RFeye Guard mean that even sophisticated devices using advanced transmission techniques designed to evade detection can be identified and located.
Critical National Infrastructure (CNI) 


Infrastructure related to energy, transport, communications, and public health is essential to a nation’s safety, prosperity, and well-being, and this has increasingly made it a target for both physical and cyber-attacks. Critical Infrastructure Protection (CIP) measures are vital to key assets such as nuclear reactors, water treatment plants, and dams.
Protection from electromagnetic threats needs to fit seamlessly into the infrastructure environment alongside physical and cyber measures to ensure that operation is both smooth and secure.
 Why In-Place Monitoring?
Why In-Place Monitoring?
The essential services provided by national infrastructures such as power plants, chemical facilities, and drug manufacturing facilities need an extremely high level of security. Cyber and electromagnetic intrusion into such a facility can be one of the easiest ways to cause massive economic damage or even large-scale loss of life.
Using a covert device to gain remote access to the network infrastructure of a drug manufacturing facility, the industrial automation systems can be controlled to dangerously alter dosages. A data exfiltration attack on a nuclear power plant can be used to find out when nuclear materials are due to be moved and the security protocols in place. By definition, an attack on Critical National Infrastructure is likely to be disastrous.
RFeye Guard is a key component of protection for the Cyber and Electromagnetic environment in and around these facilities. The system will monitor the RF spectrum in real-time, allowing potential threats to be located, removed, and investigated.
However, these kinds of attacks designed to do immediate damage are not the only threats that CNI facilities face. RFeye Guard can also be used to prevent the use of eavesdropping devices related to industrial espionage as well as accidental RF interference to industrial automation systems.
Commercial offices 


Companies win commercial business through their employees’ ability to talk, develop, design and plan. From board rooms to engineering labs, critical tactical and strategic decisions are made and discussed in great detail. This is why, in modern business, security has to be a key area of focus. We are all familiar with the need for network security to keep intrusions out, which is perhaps why so many security breaches take place inside the organization.
 Why In-Place Monitoring?
Why In-Place Monitoring?
With IP crime related to the theft of trade secrets costing the US economy alone $180 billion a year, there is a growing need for organizations to protect themselves against state-sponsored and competitor-instigated industrial espionage.
In a busy work environment, the traditional method of carrying out TSCM sweeps on a periodic basis is not feasible. The level of activity around the office means that a sweep is only really valid for the time it takes place. It is far too easy for an employee to reactivate electronic surveillance or data exfiltration device after the sweep team has left or, indeed, for the evening cleaners to place devices at the request of a competitor or foreign government. TSCM sweeps are also highly disruptive to work and will usually require equipment to be switched off.
RFeye Guard can monitor your facility or secure meeting room 24/7 and in real-time to detect RF transmissions that may compromise office security. This system works autonomously in the background with an alert and location provided to security guards if/when a suspect device is detected. The system can be integrated with third-party security systems to provide an overall security picture. Often, this will allow RFeye Guard location data to be cross-referenced with other sources such as CCTV to identify the employees responsible for placing covert devices.
Data centers 



Data center operators trade in trust. The ability to maintain services and assure data continuity alongside security is essential. Owner-operated data centers need to deliver the same level of service and also consider security as a primary function. Internal data services are more likely to be used for IP or business-critical data and processing. Reliance on centralized infrastructure is growing as cloud services and virtual desktops become the default computing medium, making security and continuity increasingly dependent on data center resilience.
 Why In-Place Monitoring?
Why In-Place Monitoring?
Security breaches in data centers can have a massive and far-reaching impact on data security and service provision. For this reason, they can have some of the strongest physical and cyber security measures in the world.
One of the easiest ways to prevent security breaches or even accidents, such as staff tripping over and pulling out a cable, is to restrict human access to the bare minimum. This usually means invasive TSCM sweeps are not an option. A system like RFeye Guard can be installed in a data center and left to operate autonomously, reporting back unusual RF activity to a remote security guard. Unusual RF activity may just be a malfunctioning component or could be a suspect transmission used for data exfiltration. Either way, a signal location can be provided, allowing further investigation.
The real-time autonomous monitoring of the RFeye Guard provides an extra layer of security without introducing any new risk related to human access to the facility.
Banking and financial institutions 


Banks and other financial institutions are entrusted with a vast amount of consumer and business money and data. In the event of a security breach, the consequences for the affected institution will be loss of reputation and patronage in the best case. In the worst case, there could be financial liability into the millions of dollars. Even where data breaches are not related to negligent or malicious activities by employees, the organization can still be found liable if regulatory authorities find that best efforts have not been made to protect data. Comprehensive cyber, electromagnetic and physical security measures are essential to minimize risk.
 Why In-Place Monitoring?
Why In-Place Monitoring?
Banks and financial institutions need a level of cyber and electromagnetic security that cannot be guaranteed by an occasional TSCM sweep. It is far too easy for a data exfiltration device to be placed or reactivated after a TSCM team has given the all clear and left.
RFeye Guard provides institutions with the 100% assurance they need enabling them to protect data, money and services to the extent their customers expect. The autonomy of the system makes it an easy way to increase security. Once a network of sensors (Nodes) is installed in a building, the system will monitor the RF space 24/7, providing an alert and location to security guards when a suspect device is detected. It can be readily integrated with other third-party security systems to form part of an overall security picture.
Guard can also be used to enforce mobile device bans on trading floors. Monitoring of all communications on trading floors is key in the prevention of misconduct such as insider trading. Since this monitoring can be circumvented if traders use their own mobile devices, some banks have begun to implement mobile bans. Employees are not always cooperative with such bans, either due to malicious activity or personal reluctance to be away from their phone. RFeye Guard will seamlessly detect mobile devices and their location in an office without the need to have intensive security measures such as searches and visually monitoring the trading floor.
Secure facilities & SCIFs 


Physical securityBug sweepingIn-place monitoring system
SCIFWhen matters of state and national security are being discussed, secrets need to remain secret. Often, these
 discussions will take place in a Sensitive Compartmented Information Facility (SCIF). A SCIF is an enclosed area (could be a room or an entire building) that is designed to protect occupants from surveillance. They are acoustically and electronically shielded and often guarded. Electronic devices such as phones or laptops are not permitted in these areas and have to be left outside.
discussions will take place in a Sensitive Compartmented Information Facility (SCIF). A SCIF is an enclosed area (could be a room or an entire building) that is designed to protect occupants from surveillance. They are acoustically and electronically shielded and often guarded. Electronic devices such as phones or laptops are not permitted in these areas and have to be left outside.
Why In-Place Monitoring?
If a phone or surveillance device was taken into a SCIF, by accident or maliciously, a previous TSCM sweep wouldn’t be effective. Security breaches need to be picked up the instant they happen, not hours or days later. An in-place monitoring system like RFeye Guard would be able to detect any device transmitting inside the SCIF the instance it happened, regardless of whether the device was brought in before or during the meeting. With RFeye Guard the security team can be immediately alerted, and the exact room the security breach occurred pinpointed. The meeting could be stopped before conversations are potentially compromised.
Embassies and diplomatic buildings 



In a world of constantly shifting social and political landscapes, it is important that nations have safe spaces to discuss ongoing events and policy both at home and outside home borders. Safe spaces must exist without fear of bugging, interception or eavesdropping technologies. These secure spaces exist within government buildings as well as embassies and other diplomatic buildings such as diplomatic residences. These environments need a solution to ensure those spaces are continually free from transmitting devices and assure absolute freedom to discuss ongoing policy, strategy or intelligence.
Why In-Place Monitoring?
These buildings need to have complete assurance against eavesdropping and other cyber and electromagnetic threats. An occasional TSCM sweep does not usually provide the peace of mind required since it is easy for devices to be switched off or moved during a sweep and reactivated ahead of an important meeting. Hostile actors are then able to gain information to be used in a manner detrimental to the nation’s security or prosperity. In such a scenario the device may be long gone before the data breach is recognized, leaving investigators unable to identify the source or prevent further breaches. Either way, identifying the damage has already been done.
RFeye Guard will autonomously monitor secure government buildings 24/7. This means a surveillance device planted immediately before a sensitive meeting will immediately generate an alarm with a location. Not only does this allow the meeting to be secured, but cross-referencing of RFeye Guard location data with CCTV or other data sources will often allow the responsible person to be identified.
The state-of-the-art software and RF specifications of RFeye Guard mean that even sophisticated devices using advanced transmission techniques designed to evade detection can be identified and located.
Critical National Infrastructure (CNI) 


Infrastructure related to energy, transport, communications, and public health is essential to a nation’s safety, prosperity, and well-being, and this has increasingly made it a target for both physical and cyber-attacks. Critical Infrastructure Protection (CIP) measures are vital to key assets such as nuclear reactors, water treatment plants, and dams.
Protection from electromagnetic threats needs to fit seamlessly into the infrastructure environment alongside physical and cyber measures to ensure that operation is both smooth and secure.
 Why In-Place Monitoring?
Why In-Place Monitoring?
The essential services provided by national infrastructures such as power plants, chemical facilities, and drug manufacturing facilities need an extremely high level of security. Cyber and electromagnetic intrusion into such a facility can be one of the easiest ways to cause massive economic damage or even large-scale loss of life.
Using a covert device to gain remote access to the network infrastructure of a drug manufacturing facility, the industrial automation systems can be controlled to dangerously alter dosages. A data exfiltration attack on a nuclear power plant can be used to find out when nuclear materials are due to be moved and the security protocols in place. By definition, an attack on Critical National Infrastructure is likely to be disastrous.
RFeye Guard is a key component of protection for the Cyber and Electromagnetic environment in and around these facilities. The system will monitor the RF spectrum in real-time, allowing potential threats to be located, removed, and investigated.
However, these kinds of attacks designed to do immediate damage are not the only threats that CNI facilities face. RFeye Guard can also be used to prevent the use of eavesdropping devices related to industrial espionage as well as accidental RF interference to industrial automation systems.
Commercial offices 


Companies win commercial business through their employees’ ability to talk, develop, design and plan. From board rooms to engineering labs, critical tactical and strategic decisions are made and discussed in great detail. This is why, in modern business, security has to be a key area of focus. We are all familiar with the need for network security to keep intrusions out, which is perhaps why so many security breaches take place inside the organization.
 Why In-Place Monitoring?
Why In-Place Monitoring?
With IP crime related to the theft of trade secrets costing the US economy alone $180 billion a year, there is a growing need for organizations to protect themselves against state-sponsored and competitor-instigated industrial espionage.
In a busy work environment, the traditional method of carrying out TSCM sweeps on a periodic basis is not feasible. The level of activity around the office means that a sweep is only really valid for the time it takes place. It is far too easy for an employee to reactivate electronic surveillance or data exfiltration device after the sweep team has left or, indeed, for the evening cleaners to place devices at the request of a competitor or foreign government. TSCM sweeps are also highly disruptive to work and will usually require equipment to be switched off.
RFeye Guard can monitor your facility or secure meeting room 24/7 and in real-time to detect RF transmissions that may compromise office security. This system works autonomously in the background with an alert and location provided to security guards if/when a suspect device is detected. The system can be integrated with third-party security systems to provide an overall security picture. Often, this will allow RFeye Guard location data to be cross-referenced with other sources such as CCTV to identify the employees responsible for placing covert devices.
Data centers 



Data center operators trade in trust. The ability to maintain services and assure data continuity alongside security is essential. Owner-operated data centers need to deliver the same level of service and also consider security as a primary function. Internal data services are more likely to be used for IP or business critical data and processing. Reliance on centralized infrastructure is growing as cloud services and virtual desktops become the default computing medium, making security and continuity increasingly dependent on data center resilience.
 Why In-Place Monitoring?
Why In-Place Monitoring?
Security breaches in data centers can have massive and far-reaching impact on data security and service provision. For this reason, they can have some of the strongest physical and cyber security measures in the world.
One of the easiest ways to prevent security breaches or even accidents, such as staff tripping over and pulling out a cable, is to restrict human access to the bare minimum. This usually means invasive TSCM sweeps are not an option. A system like RFeye Guard can be installed in a data center and left to operate autonomously, reporting back unusual RF activity to a remote security guard. Unusual RF activity may just be a malfunctioning component or could be a suspect transmission used for data exfiltration. Either way, a signal location can be provided, allowing further investigation.
The real-time autonomous monitoring of RFeye Guard provides an extra layer of security without introducing any new risk related to human access to the facility.
Banking and financial institutions 


Banks and other financial institutions are entrusted with a vast amount of consumer and business money and data. In the event of a security breach, the consequences for the affected institution will be loss of reputation and patronage in the best case. In the worst case, there could be financial liability into the millions of dollars. Even where data breaches are not related to negligent or malicious activities by employees, the organization can still be found liable if regulatory authorities find that best efforts have not been made to protect data. Comprehensive cyber, electromagnetic and physical security measures are essential to minimize risk.
 Why In-Place Monitoring?
Why In-Place Monitoring?
Banks and financial institutions need a level of cyber and electromagnetic security that cannot be guaranteed by an occasional TSCM sweep. It is far too easy for a data exfiltration device to be placed or reactivated after a TSCM team has given the all clear and left.
RFeye Guard provides institutions with the 100% assurance they need enabling them to protect data, money and services to the extent their customers expect. The autonomy of the system makes it an easy way to increase security. Once a network of sensors (Nodes) is installed in a building, the system will monitor the RF space 24/7, providing an alert and location to security guards when a suspect device is detected. It can be readily integrated with other third-party security systems to form part of an overall security picture.
Guard can also be used to enforce mobile device bans on trading floors. Monitoring of all communications on trading floors is key in the prevention of misconduct such as insider trading. Since this monitoring can be circumvented if traders use their own mobile devices, some banks have begun to implement mobile bans. Employees are not always cooperative with such bans, either due to malicious activity or personal reluctance to be away from their phone. RFeye Guard will seamlessly detect mobile devices and their location in an office without the need to have intensive security measures such as searches and visually monitoring the trading floor.
About
T S C M
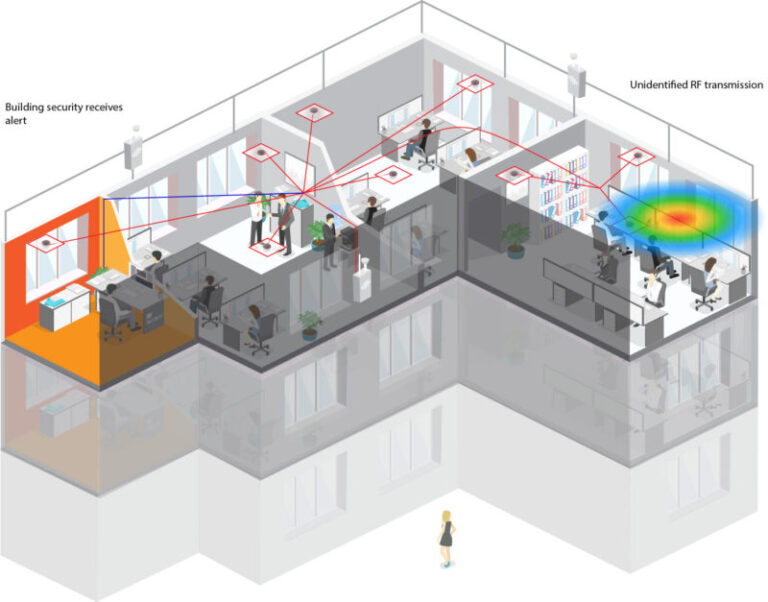
What is continuous TSCM?
In order to fully protect your facilities from the threat of illicit surveillance devices, a persistent in-place monitoring system is essential. Traditional TSCM strategies, such as bug sweeping, may be able to locate an unauthorized RF transmission at the time of the sweep. However, what if the bug is placed after the sweep has taken place? What if the bug only transmits for a few seconds in the middle of the night? What if the bug is frequency hopping, or the signal is “hidden” close to another high-power signal? A traditional bug sweep may not be able to locate these unauthorized transmissions, leaving you exposed to potential security breaches.
The RFeye Guard continuous TSCM system relies on a network of permanently installed, but discreet, RF receivers (RFeye Nodes) that are continuously scanning and sweeping the RF spectrum for unauthorized transmissions. If an illicit signal is detected, the location of the signal is calculated using Power On Arrival (POA) and an alert raised. This can then be displayed on the RFeye Guard software in order for further investigation work to be carried out
Professional Sercurity System
Secure Your Place From Top to Bottom
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Testimonials
What They’re Saying
Here are some cool things our clients have to say about How they feel about our Quality Service
ChipScape and Security Systems have installed CCTV security surveillance systems at our organization. We are satisfied with good service and solution provided by the company. We wish all the best for the future endeavors.
ChipScape Security System have successfully installed tested and commissioned CCTV based surveillance cameras at our institution premises and the quality of the product supplied match exactly our specifications and requirement and the entire system is working for our satisfaction.
Asked Questions
Frequently Asked Questions
Eros consequat tellus viverra dictumst habitant. Sociosqu letius interdum cras mus sagittis potenti suspendisse dis quam. Sed posuere enim nam accumsan proin vivamus nunc.
Global Questions
Nunc ante cursus proin efficitur semper est. Vestibulum per velit consectetuer suspendisse quis orci congue urna integer dictum. Habitasse quis auctor class semper volutpat rhoncus natoque.
Nunc ante cursus proin efficitur semper est. Vestibulum per velit consectetuer suspendisse quis orci congue urna integer dictum. Habitasse quis auctor class semper volutpat rhoncus natoque.
Nunc ante cursus proin efficitur semper est. Vestibulum per velit consectetuer suspendisse quis orci congue urna integer dictum. Habitasse quis auctor class semper volutpat rhoncus natoque.
Nunc ante cursus proin efficitur semper est. Vestibulum per velit consectetuer suspendisse quis orci congue urna integer dictum. Habitasse quis auctor class semper volutpat rhoncus natoque.
Nunc ante cursus proin efficitur semper est. Vestibulum per velit consectetuer suspendisse quis orci congue urna integer dictum. Habitasse quis auctor class semper volutpat rhoncus natoque.
Don't wait for intruders to enter your house
Install your cctv now and get 25% discount for this month



